So, the bad guys got your FTP password…
And perhaps this wasn’t the first time. Often you’ll see this same issue on multiple accounts before you start to see the trend. So, how do you protect yourself?
First of all, does he really know the password?
The simplest way to check to see if the bad guys used your FTP password is to simply check the logs. On cPanel servers, the logs are stored in a directory called access-logs. Here’s an example:
##file: ftp.example.com-ftp_log
Sat Apr 27 12:21:31 2013 0 208.80.11.- 2332 /home/joe/www/index.php a _ o r joe
Sat Apr 27 12:21:31 2013 0 208.80.11.- 2661 /home/joe/www/index.php a _ i r joe
I highlighted a couple of interesting fields. The IP address of the user (I intentionally left off the last digit to protect the guilty), the size of the file, and the direction of the transfer (in, or out).
Note that the file is first transferred out (downloaded), and then transferred back in (uploaded) at a larger size. That tells us that they added something (typically some sort of advertisement redirection code).
The other thing is the IP address. It should be sufficient to note that this address isn’t YOUR address. But sometimes you don’t know for certain. So let’s look up this IP address over at domaintools.com:
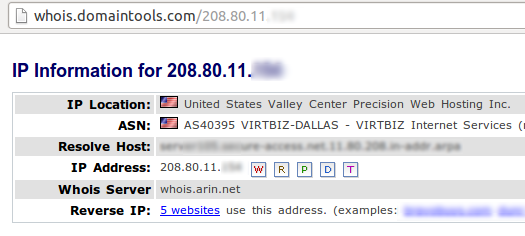
It’s pretty clear that this address belongs to a hosting company, and indeed domaintools knows of 5 different websites using that address. We can be fairly certain that at least one of those sites has been hacked. Most attacks will come from hosting companies or from overseas (and frequently overseas hosting companies), which makes this a pretty big red flag.
We probably should notify the abuse@ address you’ll find down lower on this same whois page at domaintools. Often notifications from people like you are how other victims find out that they’ve been hacked.
So, we know that the attacker came in through FTP, which means we know that he knows the FTP password. But since you used a strong password (right?), then we know that he didn’t guess it.
So how did he get it?
The bad guy got your password from someone who knows it. Maybe you, maybe your boss, maybe your offshore developer. The key is password-stealing malware. It’s a virus. Or something like it.
While this has always been a possibility, we first saw trend really take hold sometime in 2009, and it has been growing exponentially since then. Typically this is malware that shows up on your computer. This could arrive through any of the common paths; right now Java is the current favorite attack method with a success rate near 100%, even against patched computers running the the latest security suites.
This malware wills scan popular programs for saved passwords. This includes programs like CuteFTP, FileZilla, DreamWeaver, all web browsers, and many others. In addition, many of these programs also will monitor your network traffic and read any passwords as they are used by your FTP program. Remember that FTP traffic is not typically encrypted, and that includes password. These login credentials then get transmitted to the attacker, and your site gets hacked.
OK, What can I do?
First thing to do is change your passwords. All of them. If the bad guys have one password, then they may have all the rest. You’ll probably want to do this from a “known safe” computer. “Live disks” are handy for guaranteeing safety, traditionally available for Linux, but now possible with Windows 8 as well.
Next you’ll want to clean up your computers. There’s no perfect way to ensure that you’ve gotten rid of the threat, other than to erase and start over. But then again, starting fresh every few years is good security hygiene. Barring that, there’s a whole multitude of security scanning and repairing and protection tools out there available for a price, and all guaranteed to find the threats they recognize.
If instead you want to switch to an operating system that is less frequently targeted by malware, you’ll certainly find that approach to be highly effective, though there’s always a learning curve worth considering.
And finally, you’ll want to protect your passwords. First and foremost, when someone no longer needs to know a password, don’t expect him to forget it: change the password. When a contractor finishes work, when an employee moves to a different project, when a marketing campaign has finished, change the passwords. When you need to “disable” an account temporarily but have to keep it online in the mean time, and effective way of preventing logins is to change the password to something long and random, and then don’t tell anyone.
Last of all, practice good security sense: don’t save the passwords on your computer unless you know your computer is absolutely perfectly safe (which it typically is not). And don’t use protocols like FTP (which don’t encrypt anything) unless you have no choice.
There you go, that’s all there is to it! Take a few precautions and you should be safe — or at least safer than otherwise. But don’t forget to back everything up just in case.